WordPress Hack
On Friday, the WordPress instance that Macdrifter was sitting on was subject to a WordPress vulnerability. I was lucky since I had already been working on moving off of WordPress. I was able to undo the malicious WordPress code within a few minutes.
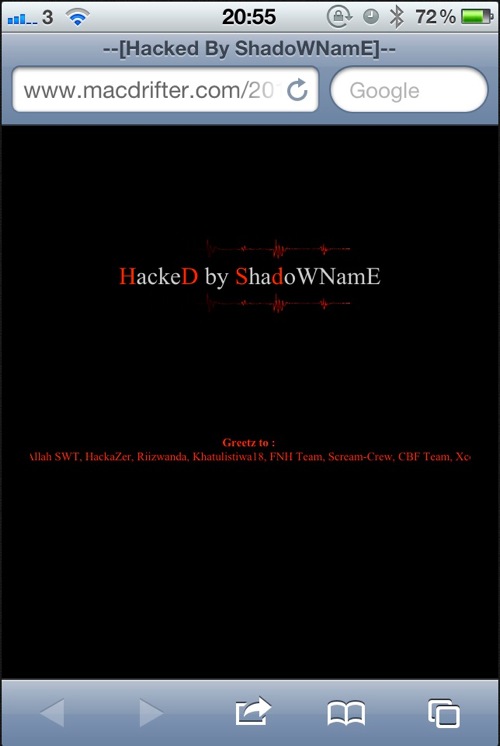
My WordPress installation is self hosted and I was on the latest version. I also use very few plugins, which are a common vector for exploits. I was able to bring back WordPress by doing the following:
- I logged in through the admin control panel and disabled all plugins.
- I took the WP application down through my host control panel.
- Connected over FTP and looked for recently modified files in the WordPress directories. Found one: index.php. This contained the injected code.
- Replaced those files from a backup.
- Browsed the WP database for recent entries and look for suspicion entries. Unfortunately many hacks use binary encoded strings to hide them. This was not helpful to me.
- Changed all SSH passwords.
- Turned the WP application back on.
- Change WP admin password.
Step 9 was to dump my entire WordPress database in several formats and then move everything to a static blog system. As far as I can tell the exploit was live on the site for only a few minutes.1
I’d like to reiterate that I do not think my password was compromised. Perhaps there was a brute-force attack on it, but that seems unlikely. I’m not a worthy target for that kind of effort. My gut tells me it was a plugin vulnerability. I’ll never know. Here’s my advice, if you run your own WordPress instance, make regular backups of both the database and all of the application files. Also, get familiar with your hosts application controls.
-
Thanks to Mark Kelly for the heads up ↩︎
