VPN and Privacy
In the United States we have few privacy protections. We now have fewer than we had 6 months ago. We represent little more than a pool of cash to be exploited. My personal strategy is to make the collection of my data cost as much as possible because I like to believe that there is a point that it loses its value to those doing the collecting.
With the repeal of the FCC rules governing collection of data by ISPs, I now use a VPN 24/7. This is a different beast from using a VPN while traveling. When the bad actor in the middle is the ISP and government agencies, there are additional considerations. I highly recommend reviewing this fantastic VPN comparison chart. Download the detailed spreadsheet to understand where the scores come from. While reviews like this TorrentFreak review provide overviews of the privacy terms, that’s only a small piece of the story. After researching several VPN services, I actually switched my provider.1
There are plenty of other niche VPN reviews out there, such as this one about Chromebook support, or this general overview. Just be aware that not many reviews concern themselves with an always-on use case and I think most of them approach VPNs as a personal security tool while traveling.
Unfortunately, the VC culture has yet to create a Tinder for VPN providers, so I had to do a lot of research and testing to pick a new host. Here were some of the criteria I used to pick a new VPN provider.
- They can not be a US company because national security letters are very powerful and easy to abuse.
- They should not log activity, including my IP address
- They should have clear and explicit statements about what they do with data
- Performance needs to be good enough for me to not notice
- They must have a US host so I can use Netflix, Hulu, and Amazon Prime streaming
- They need to support multiple devices with one account. Mine supports up to 6 which covers most of my needs
- They should allow me to configure a router to use their service
- Setup should be easy or it needs to need zero tweaks once configured. My spouse does not need to know about the VPN running on her phone or laptop.
There are plenty of good VPNs out there. Many use the OpenVPN iOS app, which is fine. I preferred some of the VPNs that have their own dedicated iOS app. Some even have very reasonable Mac apps.
Setup
Here are some suggestions based on my experience of testing and changing VPN providers.
If you installed a VPN profile on your Mac or iOS device, delete it before you switch to a new provider. In several cases, the new provider was overridden by the old profile. Even worse, on one occasion, the custom app and the OS declared I was connected through a VPN but my IP address was still clearly visible to my ISP.
Confirm that your VPN is working by checking to see what your public IP address is. Every time I changed services or settings I checked my IP. This is the easiest way to know if you are exposing your traffic to your ISP.
Check to see if you’re leaking through IPv6 when on your VPN. I don’t fully understand what’s going on here but my research has lead me to believe that some VPNs leak enough information that it becomes trivial to snoop. Remember, the goal isn’t to be as secure as Trump-Putin direct line. It’s meant to make it cost a few extra pennies to snoop.
Use one speed test service for all tests. They may not always be accurate but I think it’s consistent and easier to compare results. I used the Ookla Speedtest service.
Performance
Using a VPN doesn’t mean that bandwidth has to be terrible. In fact, I had enviable bandwidth with several VPN providers. The Ping always takes a big hit but in actual use I don’t notice it on my Mac.
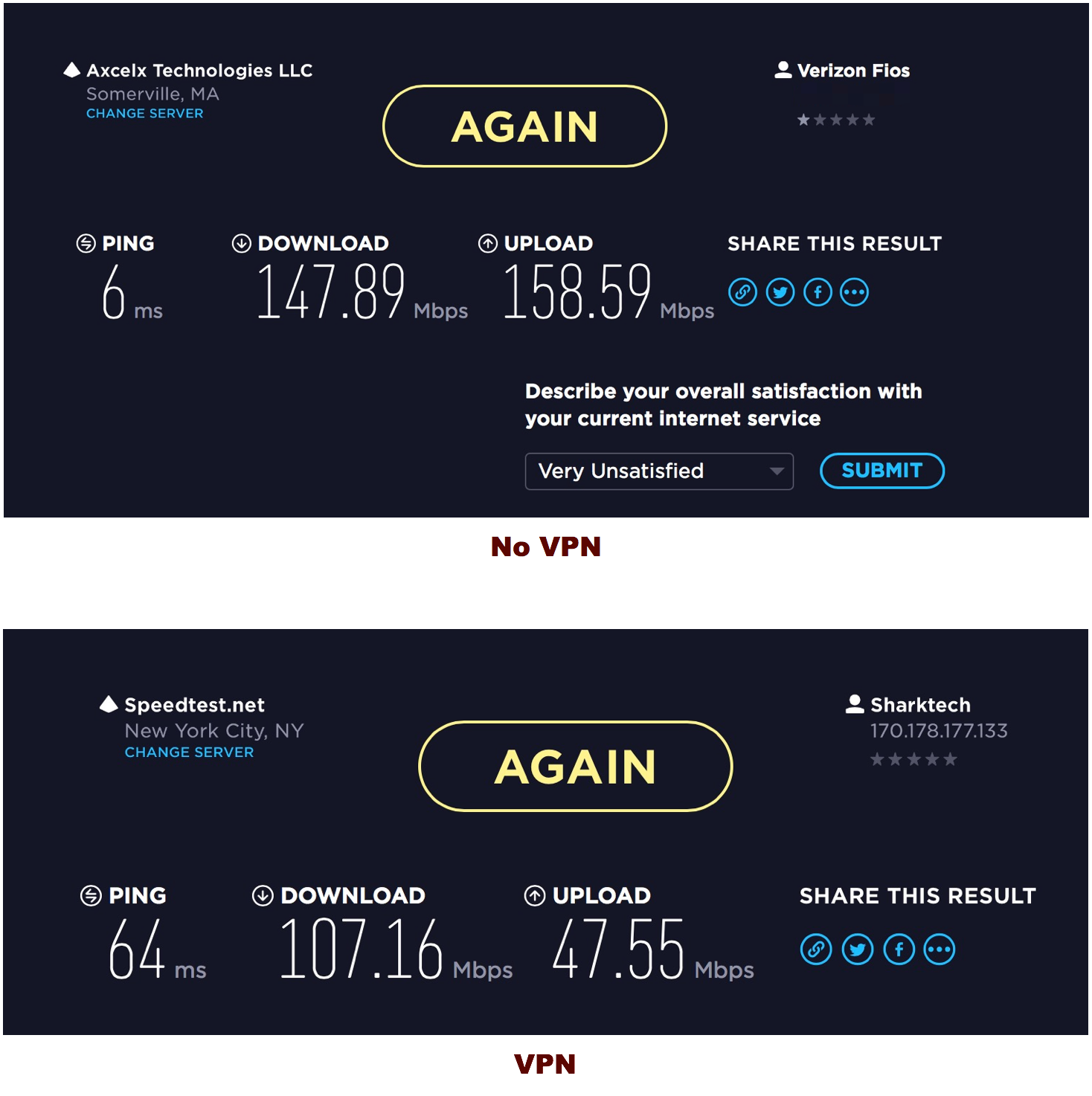
I use Verizon for my iPhone and the VPN has been just fine. It’s not noticeable. Even on WiFi it’s not noticeable. I leave the VPN turned on whenever my phone is on.
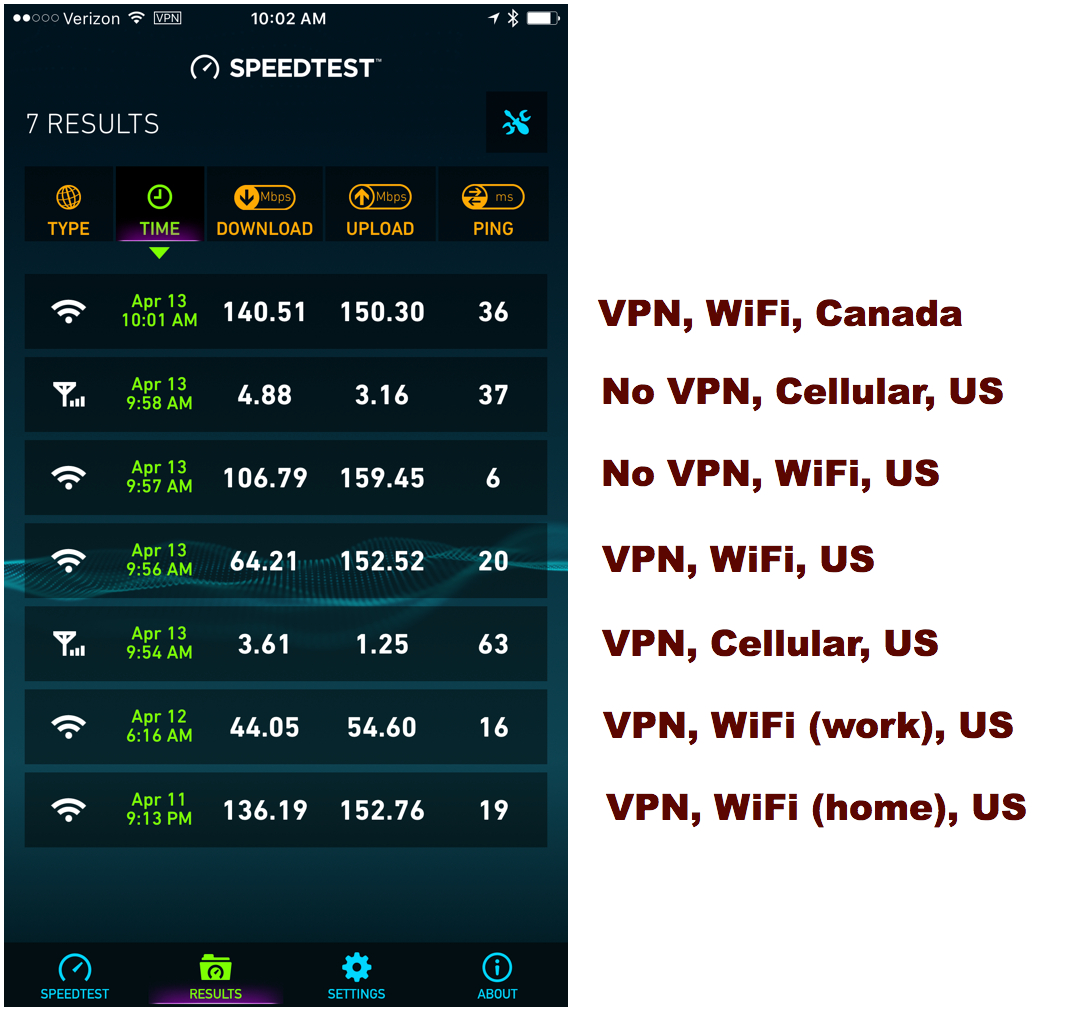
As that image helps to illustrate, the closest VPN host is not necessarily the fastest. With my preferred VPN provider, Canada has better performance than their US host. It’s really just a matter of testing for yourself.
Background
Here’s a little background on what’s going on and what a VPN might get you.
Bruce Schneier is about as pessimistic as I am:
They can snoop through your traffic and insert their own ads. They can deploy systems that remove encryption so they can better eavesdrop. They can redirect your searches to other sites. They can install surveillance software on your computers and phones. None of these are hypothetical.
Brian Krebs is seems more realistic but on a second read I think he’s just saying everything about ISPs and user privacy was already terrible. It’s just now we know that no one in congress cares.
As shocking as this sounds, virtually nothing has changed about the privacy of the average American’s connection to the Internet as a result of this action by Congress, except perhaps a greater awareness that ISP customers don’t really have many privacy protections by default. The FCC rules hadn’t yet gone into effect, and traditional broadband providers successfully made the case to lawmakers that the new rules put them at a competitive disadvantage vis-a-vis purely Web-based rivals such as Facebook and Google.
later…
If you just want a VPN provider that will keep your ISP from snooping on your everyday browsing, virtually any provider can do that for you. But if you care about choosing from among VPN providers with integrity and those that provide reliable, comprehensive, trustworthy and affordable offerings, you’re going to want to do your homework before making a selection. And there are plenty of factors to consider.
Adi Robertson from The Verge also has some interesting things to say about VPN:
The right VPN can protect against lots of things, including government surveillance and malware. But the tool isn’t a magic privacy bullet — in fact, experts can’t even agree on a great VPN service, beyond one you make yourself. While a huge number of companies provide VPNs, many have potential security flaws or could put your data at risk. It’s also difficult to tell how secure a VPN actually is, and what it’s doing with your data. So what are you supposed to do if you want to use one? The short answer is to avoid free services, and if you consider yourself tech-savvy, look into setting up your own. Otherwise, make sure a paid VPN has a privacy policy you’re okay with, and can handle the threats you’re relying on it to protect you from. And on a larger scale, remember that the best solution is still policies that would tackle the problem at the source: ISPs’ ability to sell your data.
I mostly agree with their take on VPN.2 Free VPN is not a good choice. But a paid service isn’t obviously better unless you do the research. But I think it’s worth stressing that a dedicated bad-actor will probably find a way to snoop your traffic. A VPN is not a Harry Potter magic spell. There’s already some evidence that an ISP can fingerprint encrypted traffic and determine the general nature, such as Netflix streaming verses an app. I have no expectation of hiding beyond all methods of attack. I just want my ISP to decide it costs too much to snoop my data for the small amount of profit they get from manipulating it.
-
No. I am not going to say what VPN service I’m using. It’s a non-US service with high marks for security. Performance is good enough for my needs. ↩︎
-
I don’t understand the point of making your own VPN unless that VPN is also on a server outside of your country. If your VPN server is sitting in your closet then it’s not really hiding your traffic from your ISP. ↩︎
